In our earlier article The Blocky for Veeam® – 5 Step Guide to a Safer Network we highlighted the importance of creating a Cyber Security Policy and Disaster Recovery Plan. A key element of this should be a communications plan which can be easily overlooked during the turmoil of containing a cyberattack and the restoration of IT systems.
Keeping stakeholders informed is an area where organizations often stumble especially when a cyber-attack has resulted in a data breach. Performing this task well requires having plans in place long before any breach of your security, but also important is rehearsing and updating this plan to ensure the most appropriate communication channels and spokespersons are always primed.
In this article we will offer some guidance on establishing a cybersecurity communications plan and outline some of the pitfalls that can be avoided.
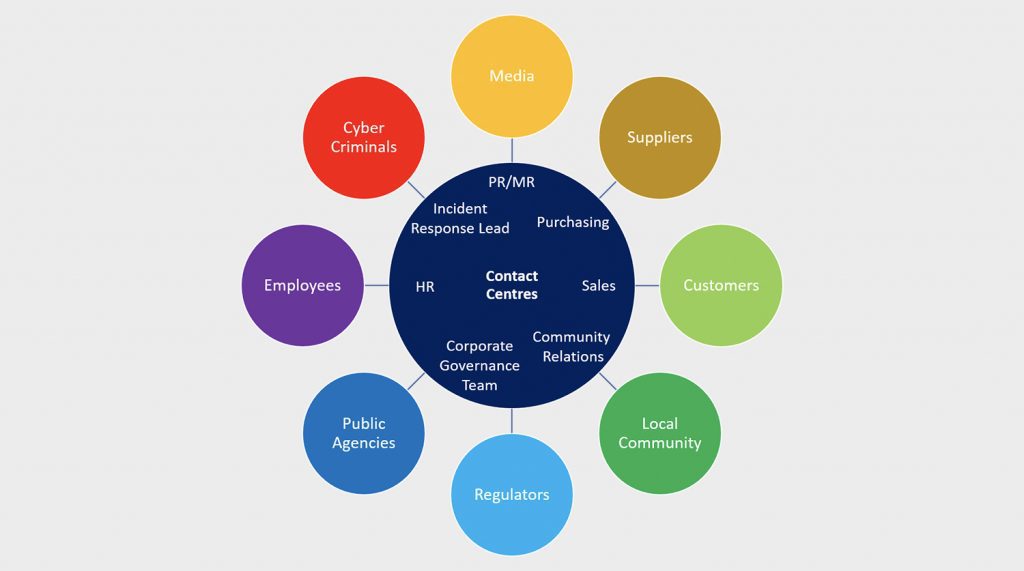
One of the primary steps of building a crisis communication strategy is identifying and understanding the audiences that the organization needs to reach during a cyberattack. Many potential audiences need to be informed during the event and recovery period. These may include employees, IT staff, customers, vendors, suppliers, investors, government officials, industry regulators and of course the media. The communications plan should set out the needs of each of the entities that require contact and identify who within the organization is best placed as a spokesperson to communicate with each audience.
Media interaction can be a vital component in the event of a cyberattack. Communicating with the media has the potential to positively affect stakeholder reactions, but this of course depends on how well the message is composed and delivered. A prompt and well-calculated announcement to the media can go a long way to reduce speculation and rumor and let your stakeholders know you are in control. If possible, work with your PR agency professionals who should be experts in crisis communications.
Spokesperson and communication team assignment
Spokesperson selection is one of the most crucial aspects of a crisis communications plan. A cyberattack will induce panic across the organisation, not just within your IT support team. This creates a high chance of blunders and mistakes under the pressure which emphasizes the need for a solid crisis communication plan with specific spokesperson responsibilities set in place. Smaller organizations may decide to have just one person in charge of communicating both internally and externally, often the CEO him/herself.
It is important that the spokesperson for a cyberattack crisis should be both technically knowledgeable and an authority figure in the business. If your spokesperson is the CEO, ensure he or she is able to speak accurately and intelligently about the technical details of the attack. You would not want your spokesperson to lose credibility by accidentally misstating factual elements of the event. People need to know that top leadership is in control and in command of the situation.
However, it may be preferential to assign a point of contact and a backup for each department with the assigned members forming part of a tightly coupled group. Additionally, a team should be identified to oversee all external communications, and that team should include the CEO. During the crisis period, a team should be on hand to answer external phone calls, check voicemails, reply to emails, provide support, and manage social media accounts.
The diagram below illustrates some of the common stakeholders and likely spokesperson alignments.
Communication channels, templates and rumor containment
After establishing the audiences and spokesperson alignments it is essential to decide how communications will take place. Companies should not rule out the possibility that their email and telephone systems could be targeted as part of an attack, so other communication options such as mobile phones or social messaging channels should be considered within the crisis communications plan. It is beneficial to have pre-created communication templates available prior to any cyberattack as they will make it easier and faster to get your message out to different groups at the right time. One way to control communication slip-ups with employees is to establish a ladder of communications within your communications plan. This chain of communication should describe who is mandated to inform who, and in what sequence. It is vital to caution unauthorized staff to not discuss the situation externally. The rumor-mill is dangerous, especially when it originates from staff. They should be well cautioned in advance to not discuss details of any cyberattack publicly, not even with friends or family, and certainly not with the media. Instead, they should refer any inquiries to the appointed spokesperson or teams.
It is certainly advisable to break the story of any major cyberattack before the media does. There have been many instances of the media reporting a cyber incident even before the CEO had been made aware. If the attack has impacted operations, it is best to own up to the issue with as much accurate information as you have at the time. Determine the size and scope of the problem before making any definitive statements. If you report inaccurate data, such as the magnitude of any data breach, you run the risk of having to backtrack on previous statements and admit the problem was far worse than expected. Sharing accurate figures regarding the scope of the incident in the face of tough questions from media will be more beneficial for you and all stakeholders in the long run. In order to stay in control of your story, know your facts and stick to them. You will need to quickly retain control of your processes and information and ensure that each line of business is aware of the crisis recovery plan and is sending all status updates and issues encountered through the appropriate channels.
Communicate a clear recovery path
Your company must demonstrate accountability and communicate a clear and timely plan for remediation. Data loss is not only harmful and expensive, but it is also becoming increasingly less acceptable to the public, so you must do everything possible to limit the damages of data loss and interruptions to business continuity. Ensure that your communications make it clear what remedial actions your company is undertaking, so your key stakeholders can rest assured their data is in safe hands. Customers are a number one priority. Monitor the situation closely and communicate regularly. Communicate both the good news and the bad. Attempting to conceal information will backfire, your stakeholders and certainly the media are not going to react well to anything but the truth.
Learn from any mistakes and make corrections
The importance of communicating the impact of any cyberattack rapidly to all key stakeholders cannot be overstated. When any cyberattack has been contained and rectified, be sure to hold a leadership debrief to review the crisis communication plan and how the company held up. This is a vital time to make any adjustments to the plan to reinforce what worked well and determine how to improve in any areas that fared poorly. It may also be valuable to share a high-level summary from the debrief with your key stakeholders so they can rest assured the company is in good hands. Hopefully, this outline has provided some useful checkpoints to consider in your crisis communications plan, and food for thought for those of you who are yet to set a plan in place.
Remember that clean and secure data backups are your best defense in the event of any cyberattack. For any questions, please get in touch through our contact form, the Blocky team are always ready to help.







Recent Comments